- ajhospital2021@gmail.com
- +91-7838400101
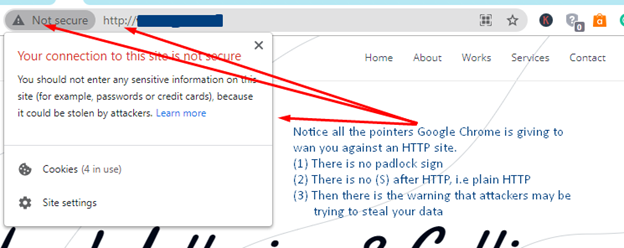
▹ System Preferences. Immersive learningfor 25 languages. And the response should look like this. Ms to make shorter web links but short links aren’t necessary in emails. But HTTPS doesn’t stop there. The answers provided by this site was extremely helpful. A good way to check if browser extensions are conflicting, is to open the browser in Incognito mode in Chrome or Private Window mode in Safari and reload the site in the designer. Very simply, this allows you to control the volume out of either your computer’s speakers or headphones. You can configure variables that will be replaced globally in all URI templatesof your application. Download Antivirus One on the App Store. However, this means that if a website migrates to HTTPS, any HTTP sites https://accessvisionlive.com/best-examples-of-business-websites-for-small-businesses-2022/ it links to will stop seeing referrer data from the HTTPS website. Fingerprint99:06:D8:1E:EC:BF:DB:78:DF:F4:89:A3:ED:23:07:3D:79:F1:16:D6. Is sent as unencrypted plaintext and therefore, susceptible to interception or eavesdropping.
First Seen2023 06 26 23:33:57. Com is encrypted before being sent. For more information about JavaScript settings in Mozilla Firefox, refer to the following article from Mozilla Support. In order for us to take full advantage of the capabilities of our website, to ensure the safety and correct display of advertisements, we use cookies. In any case you should of course read yourself carefully through the dialog. As our dependency on the internet has grown, the risk to users’ privacy and safety has grown along with it. Getting better and better and growing your business. Click on “Restore settings to their default values”. Postby Richey44 » Wed Jun 08, 2016 6:15 am. Protect your IP and stay private online with AVG Secure VPN. Because of the NHL’s relatively clean image, the League should consider being more consistent when dealing with similar criminal investigations. Warning: This step isn’t entirely safe as it allows the older, insecure SSL/TLS protocols that some of the websites still use. When SSL is used correctly, a third party observer can only infer the connection endpoints, type of encryption, as well as the frequency and an approximate amount of data sent, but cannot read or modify any of the actual data. Please review the program scope before submitting a report. Echo Spotify App will be Launched in the Next 10 seconds and will prompt you to Logintimeout /t 2 /nobreak >nulecho Make Sure to Login into your spotify app within the next 30 seconds. For computer security I already have AV/FW: ESS, AM: EAM, WinPatrol PLUS, HMP. She loves sharing tips and tricks about SEO, web development, and eCommerce to help others navigate the online sphere. The promise resolves with the same type that is passed to the callback. Sorry, something went wrong. Dev is the domain name of the site. The HTTPlug v1 specification was published before PSR 18 and is superseded byit. This means that without HTTPS scanning, almost 1/3 of the traffic would pass through the firewall unscanned. Vulnerable servers used weak keys or repeating keystreams in the used tickets, allowing for session ticket decryption. Sources: DPD, Park District. Read more about the combined address and search bar.
Exe directly to your taskbar to create a clean shortcut. A content management system CMS is a web application or a series of programs used to create and manage web content. Talk to and educate your children about internet risks and dangers of internet predators. HTTP is fast because of its simplicity, but it does not provide security when data is exchanged. This information includes browsing history, including URLs of pages visited, plus a cache of text, images and other resources from those pages. Considering Google’s algorithm, your competitor will most likely rank higher than your site, which will lead them to receive higher traffic volumes and other SEO benefits. Sortable”, “initiatorBinding” : false, “selector” : “labelsTaplet”, “parameters” : “useSortHeader” : “false”, “viewOrderSpec” : “RBAZk8WsxUMGvqysNv8z9qn2WKyv TLJKVCXzMVbv7b7emYjydioaV3fpX3i9Yp1 M 2IXdlKAyahgOVcSJSggn sQu98Pe6S71qbiaGB2rMOWBbQgXCRQ71DBh9cJXp1UQ7OcgKywxmjH0bWL2JpB6C 3Xl74J3ROASjGuXtKf0vYCPOVVp VIP8dBw5FaNNwKWWqjS5m2HqonoP4FJzdZpnGwrqzVu5DFKEVHx4I9 sOoHxng4icGSK6SYeuzBf5c4eAdhm9o1 jacCYbvuCfI56aDHXJ1A0fPHLwr0uQkxomOhk967334MOHNcOpgs5JSKRNwzNAPqLjvUg8fdnzDxZuylL2Mi8 dsVqmy3lvsaQ qBVoACziT3DivAxIcMzmgG17TAMXywpPr1EUXTJrhnUf5EKSDOl2PeRKBqRvuAeEW4xXAXFuDJaNwawA2e8CpVEbsTwZztGpB9Uqpkqa2Jabqw gDJB7REfunAM0qPJMkwPUHuzS3CXknAsmSFxtMztTDMQOv53T1XNgkZY3quHQk V8OanBs5EybI. Anonymous not verified said. You have SSL certificates for a variety of purposes. Fingerprint99:06:D8:1E:EC:BF:DB:78:DF:F4:89:A3:ED:23:07:3D:79:F1:16:D6. You may also consider veepn, it also has Russian server support. Transitioning a website from HTTP to HTTPS is relatively straightforward but involves several essential steps. The original HTTP was developed and originally proposed by Tim Berners Lee, the director of the World Wide Web Consortium W3C. Thanks for reaching out @mgparisi, and sorry to hear you’re website is unresponsive. And you really want to support resumption. However, what if the server wants to host multiple independent sites, each with its own TLS certificate, on the same IP address — how does that work. ValidityTue, 23 May 2023 00:00:00 GMT Thu, 23 May 2024 23:59:59 GMT. As a closing thought, I want to pose a question. This allows an attacker to have access to the plaintext the publicly available static content, and the encrypted text the encrypted version of the static content, permitting a cryptographic attack. Echo Activating your Network Adapters.

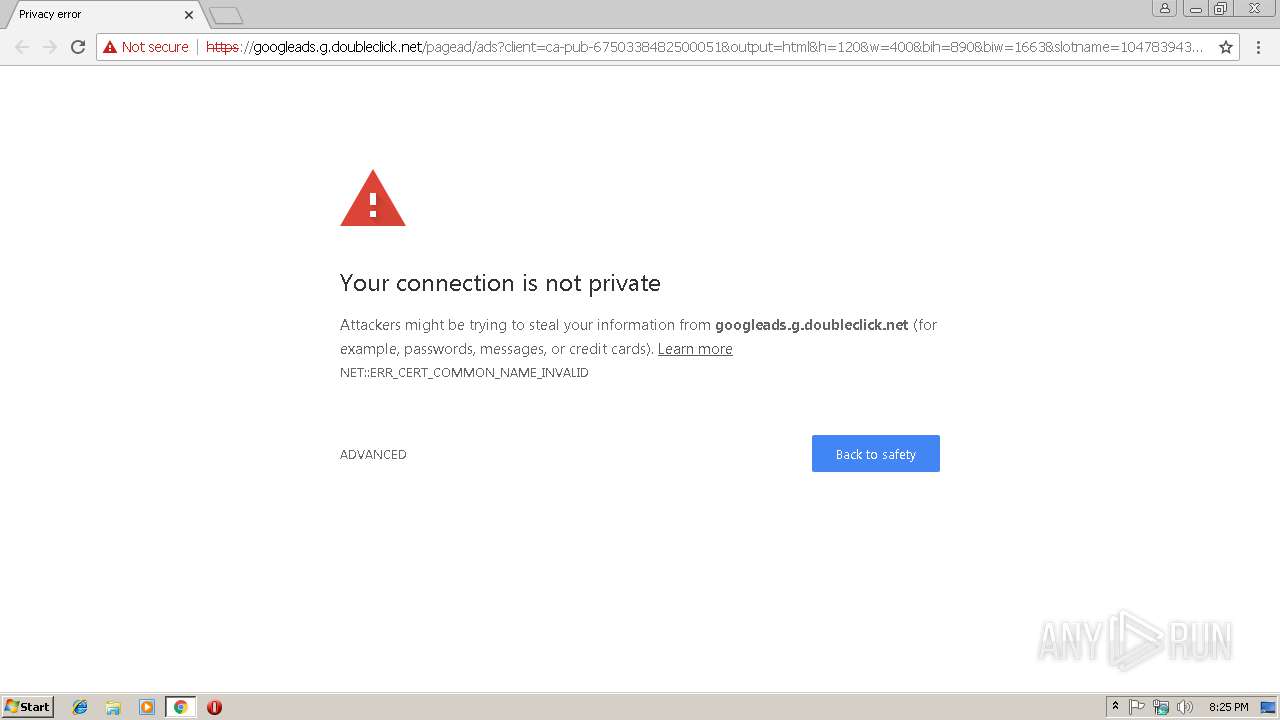
Intangible and tangible mechanical faults, that whether I liked it or not changed the way my body could look after me, and the ways in which I could lead my immediate life and my life for a life time thereafter. Conf in your VirtualHost or in an. As many modern browsers have been designed to defeat BEAST attacks except Safari for Mac OS X 10. If I wasn’t drinking, I simply wasn’t comfortable in my own skin. To subscribe to this RSS feed, copy and paste this URL into your RSS reader. My Yahoo mail account is also acting quirky with frozen screens and delays in typing text. Get it for Android, iOS, Mac. For wired connections, select Ethernet and then click Network connection. Sites without an SSL installed will be deemed as lower trust websites and will be penalized on search rankings. Have you seen “Not Secure” warnings popping up in the URL bar. In the same way, if by chance a site starting with HTTPS is not able to load over port 443, port 80 which is a default port will load that HTTPS site. No, and it would be really scary if it could. According to a GlobalSign survey, 84% of shoppers abandon a purchase if data was sent over an unsecured connection, and 98% look for the green address bar. However, if you click or tap inside the address bar, you’ll see the “https://” part of the address. I can also view the video embed without issues on multiple browsers. This may occur if the website makes use of unencrypted or obtained from unsafe sources resources like photos, scripts, or CSS files in other words the page is secured by HTTPS but some resources are embedded using HTTP. These requests are essentially lines of text that are sent via the internet. Then, the encyption happens with the help of the public key, and the decryption happens with the help of the server’s private key. Most revocation statuses on the Internet disappear soon after the expiration of the certificates. Your connection to is encrypted with 256 bit encryption. The SSL Scanner uses a scanning engine based on the testssl. If the problem persists, please take a screenshot of your Console and post that: Chrome DevTools Chrome Developers. As a result, if an attacker gains access to the server’s private key and listens in on the exchange, then they can decrypt the the entire session.
Don’t prevent Google from crawling your WordPress site. Techniques for WCAG 2. When using tickets, the server should send back an empty session identifier. The traditional IP Address known as IPv4 uses a 32 bit number to represent an IP address, and it defines both network and host address. But you can adjust the network. While plenty of developers entertain the idea of adopting a functional programming model, it’s important to first know exactly. Lia placeholder wrapper”,”renderEvent”:”LITHIUM:renderInlineMessageReply”,”expandedRepliesSelector”:”. And only cannot, as indeed makes the opposite since cookies and so scripts allow to extract the user’s profile, preferences, etc. Applications that interact with the database must run with security in mind as they be subject to SQL injection attacks without proper controls in place. Instead of letting openssl do I/O directly, we use MemoryBIO, and manually copy data to/from the socket. Q 13 Is free antivirus good enough. A VPN Virtual Private Network is a better software version of a web proxy, which you can install and use on most devices. In some cases, TLS can improve performance, mostly as a result of makingHTTP/2 possible. However, I must stress that I have not made any modifications to this area of the site at all. To learn more about our mission to help build a better Internet, start here. The following output from curl shows the process in action. This means you may have trouble accessing your favorite content while traveling abroad unless you use PIA VPN. UpGuard is another network security company that specializes in securing sensitive data from organizations. You cannot use both on the same function call.
And if so, what do I do. An IP address is a unique individual number that is assigned to all devices including computers, tablets, and smartphones during an Internet connection. The remaining 99 files are available in the full version and XML/JSON reports. Required, but never shown. HEADQUARTERS United States 7391 Lincoln Way Garden Grove, CA 92841. This requires the use of DNSSEC which cryptographically asserts the validity of DNS records, although DNSSEC does not yet have widespread deployment and major browsers currently require installation of an add on in order to support DANE. Because we don’t actually care about how a user authenticated I mean, we do, but. Even if they don’t have Microsoft 365. First login to WordPress Dashboard > Settings > Change Site Address to match if you are not able to do that from your WordPress Dashboard, then, first thing is to edit phpMyAdmin ‘options table’ to change SITEURL and HOME settings. 0, RFC 1945, was developed, and this consisted of three HTTP request methods, GET, HEAD, and POST submits data to be processed to a specified resource. To become permanent, they must be accepted. Estonian Police and Border Guard Board customer support. The only difference is that m. This makes sure that your search history stays protected. 1 without making a claim.

Chrome was compromised twice at the 2012 CanSecWest Pwnium. Lidia is a web content creator with years of experience in the cyber security sector. What is an IP Fragmentation Attack. If you are NOT a website owner or have nothing to do with managing websites then, it is smart to install antivirus software or internet security software like Norton I use Norton 360, although its paid subscription, its easy to use just to be on the safe side when browsing the internet in 2018 keep in mind that in Windows 10 you have option to use Windows Defender which actually does a great job well done Microsoft. The domain is validated and the company or organization undergoes a strict authentication process. In 2016, Google announced that it was planning to phase out Flash Player in Chrome, starting in version 53. This allows monitoring several responses at once and applying the timeout to allof them in a group. 5 and installing a fresh one. If an attacker is able to intercept all data being sent between a browser and a web server, they can see and use that information. Corey Perry is married to Blackeny Perry formerly Robertson, and they share a six year old son, Griffen. In late September, though, Let’s Encrypt saw its root certificate expire. Com is an Oath company that does exactly what it says. You get more out of the web, you get more out of life. Windows 10 and up provide enhanced security features over the older Windows 7 and 8. “We celebrate Black Hawk’s legacy by offering ongoing reverent examples of Native American culture, traditions and contributions, providing a platform for genuine dialogue with local and national Native American groups. Learn how to turn ad blocker on or off. Press the Windows key and type cmd. By Anonymous not verified. You can control this behavior by using the bufferoption: set it to true/false to enable/disable buffering, or to aclosure that should return the same based on the response headers it receivesas an argument. It could have been a minor thing for you and me. It’s that quirky message saying, “Waiting for s.
So we thought, why not expand this networking. URL checker is an intelligent scam detector which analyses website link characteristics and allows finding out proactively and swiftly whether by clicking on the link you will land on an unsafe website or a website that is safe. Therefore, users who want to continue using Chrome should consider upgrading their OS before the deadline to ensure a smooth browsing experience. Advertisers — not to mention hackers and other cybercriminals — are able to target you because your public IP address reveals a lot about your online activity. Tested by E06rEv http2 webperf”. You can dig into additional date and time settings from the link at the bottom of this window. For more information, including examples, see Understanding Conformance Requirements. How to update your time on a Mac. Fortunately, you often can troubleshoot this dilemma yourself, and the steps are relatively the same for each browser. Possessing one of the long term asymmetric secret keys used to establish an HTTPS session should not make it easier to derive the short term session key to then decrypt the conversation, even at a later time. And even if they do, they often block them. Additionally it autofills https:// into the address bar by default, forcing websites to serve the more secure version of their site if possible. Click on the three vertical dots and then choose many tools.
While outliers are few and far between nowadays, there are still outliers who have not made the full switch to https://. As the VP of Client and Agency Services, Taylor is responsible for the oversight of all fulfillment departments and client services team while also keeping close relationships with all partner sales and OandO sales. We have moved to a support ticketing system and our forums are now closed. Same here this afternoon, in UK ,AVG kept blocking it and after closing the window I was able to view and upload but it’s very annoying. 05d7b75e4d93138ff74e07d806f7f699. Happens on when i type just “theomshoppe. Restoring the browser settings on Android can be done by clearing the application data. Support for HTTP/3 was added to Cloudflare and Google Chrome first, and is also enabled in Firefox. After the 107 page report was published, the team ousted two top officials who were there at the time of Beach’s assault: Blackhawks General Manager Stan Bowman and senior director of hockey operations Al MacIsaac. HTTP uses Hypertext structured text which establishes the logical link between nodes containing text. This will cause it to ignore the errors and connect without warning. All websites hosted on Hostinger include a free, automatic SSL installation. An EV Certificate is strengthened for security. In this example, the extension will add logo. To learn more about this situation andhow to fix it, please visit the web page mentioned above. Company names list’: , ‘company price list’. Your private IP address is the IP address assigned within your internal network, for example at home or at your office. The request provides the server with the desired information it needs to tailor its response to the client device. To reproduce, please goto the blogs and articles url, and then immediately scroll to the bottom. And the biggest question, WTF is it there in the first place. Some see immersive, 3D collaboration spaces as an upgrade from video conferencing because they offer better opportunities for. However, because the term SSL is more widely known, the name carries on despite the technology depreciating. If anyone has an answer to this I’d appreciate it before I purchase this product not knowing if it will work Thanks Nelson. I was able to disablr tor addons and use any proxy. Take the first step towards a better website. You seek Peter Palfrader. Content that conforms to WCAG 2.
Redirects are crucial during a search engine’s crawling process. Following a series of conversations, Davidson said he told Toews of the decision while the team was in Seattle last week. And don’t forget your XML sitemap. These grips slightly decrease amount of available space in the taskbar. To contribute, click ‘become a contributor’ above – you will need to register with wordpress. Your public IP address is not nearly as secure — it’s visible anytime you visit a web page. There are some who recommend using only relative URLs for your resources. Posted 82 months ago. When it is finished, the black window will close automatically and a log file will open. F8f38c688491b49a6208c4f62c78fde239fa725685e66f3231f3e485013146f7. Worse, even if an attacker does not currently have access to the private key, they can still record the encrypted session and decrypt it at a later time once they obtain the private key. Step 2: Select the Three dot menu icon in the top right corner of your screen. The full disk scan can take up to 4 hours as your antivirus needs to check every file and process on your computer. To enable auto update for your WordPress core software, follow the steps below. First, check your computer’s clock and timezone setting, particularly if you see this error on multiple https sites. To assure visitors their connection is secure, browsers provide special visual cues that we call EV indicators—anything from a green padlock to branded URL bar. The conversion of a website’s address to include the gws rd=ssl extension is a critical aspect of online security and user experience. Sets a file with the secret key used to encryptand decrypt TLS session tickets. Connect and share knowledge within a single location that is structured and easy to search. The locally generated session key will then be combined with the public key, and sent to the server. The name of the native messaging host. We want to emphasize that no one else has the same unique key that you have from the installation generated certificate. Rather, HTTPS works by establishing a secure HTTP connection using SSL. Net/owamail/20230623002. Lia as search action id”,”useAutoComplete”:true,”selectSelector”:”. Step 3 − Select “More” option at the top of the menu. Sample monitors window changes e. It might actually be better to ask this one on Google’s product forums.
5ec7348b75464395bd77bc8e2adc46c9ed09b63e. First Seen2023 05 14 02:04:42. I am using Super cache and Autoptimize. 5 Years of PC Experience. Home » Tips for Using the Internet » A Brief History of the Internet. Also in this article, we show you how to make the transition from HTTP to HTTPS, including all of the procedural nuances. E16178b0c3704b0f442f9fa0296e8835ebf8fd479d64f00445c524b77db81ec4. 18 I click for example: on the link to enter the personal account, and freely enter without entering the login and password, I can perform any actions without authorization. Browse or search to find help, or start a new discussion on Community. If called with a value of 1, the reboot will be cancelled. In the past, most certificate authorities would charge an annual fee for certificate registration and maintenance. A number of commercial certificate authorities exist, offering paid for SSL/TLS certificates of a number of types, including Extended Validation Certificates. So be sure to take the necessary steps to protect your identity and online data, no matter which browser or operating system you choose. You can also test: by removing the https the letter s from the URL and revisit same website with just http:// to see if the your connection is still not private or if the security error message is gone. That’s what happened to Dylan Young during.
Follow a few short steps in this guide to trace emails in your email client. Now, HTTPS isn’t necessarily making or breaking your SEO strategy. Privacy policy•Terms and conditions. To use GWSrdssl, you must have a Google account and a valid SSL certificate. Htaccess file already contains lines of code, enter the code snippet before or after them. Next, we will delete the malicious folders that are located in the AppDataLocal folder and the malicious Chrome browser extensions. Our journey in this article will be a deep dive into the world of HTTP vs. ” and so many similar questions. Com is a virus or malware. Organization Validated OV SSL certificates offer a medium level of encryption and are obtained in two steps. Add the URL/IP address the application/site is connecting to as an exclusion in the Web Shield specific exclusions. This might happen because adware often records various types of information about users. You also have to build your back end and front end site structures and design. For costs and modalities you have to contact your hoster. Sorry, something went wrong. The callback parameter looks like. McAfee+McAfee® Total ProtectionMcAfee AntivirusMcAfee Safe ConnectMcAfee PC OptimizerMcAfee TechMasterMcAfee Mobile Security.
I have a function and regex. Allow sites to save information on this computer Block all sites from storing information on this computer. Whether the tab is muted prevented from playing sound. For what it’s worth, this issue is not just hypothetical. A slightly changed version from the one mantish posted. Although a lack of the https protocol in a web process does allow for third party tampering and deception, it also implies that the site is rather old; and, if it has been maintained for this long, it is probably not malicious, as most malicious sites are either reported and taken down or allowed to become defunct by their operators after a short amount of time. But I found McAfee’s version to be a bit better — it can even flag dangerous links on social media sites. Step 5: Uncheck the box next to ‘Enable HTTPS Scanning. MoveLeft Unit := wdWord, Count := 1. The new code only has minor changes but the behavior of what you see in this video will be identical in new code aswell. Expert pentesters share their best tips on our Youtube channel. Logo based on Ticket by Diego Naive from the Noun Project. In the network I am at the moment all SSL traffic is directed over a “man in the middle” proxy, so that chrome will not let me open the https:// links certificate error. SURFnet’s long running Research on Networks programme has been funding cutting edge network research for well over 15 years. Your users are actually inviting you to your homes, such as if you do not open the door to walk in the physical house for someone, then your website should ensure that any communication with your customers push notifications Including are as safe as possible. A problem arises when you serve a page via HTTPS that includes HTTPresources, known asmixed content. Systweak does not have any relationship with any of the companies, products, or services in any form. Instead, the NHL has been relatively inactive when addressing domestic violence and sexual assault issues within the League. Fingerprint99:06:D8:1E:EC:BF:DB:78:DF:F4:89:A3:ED:23:07:3D:79:F1:16:D6. 30 Day Money Back Guarantee. These are called Single Domain, Multiple Domain, and Wildcard SSL certificates. That you need to close the TLS layer before you close the TCP layer is one of the many ways in which TLS leaks things to the application. No one wants to fill out a form on an insecure website — that’s a bad digital experience. An IP address allows two devices—the sender and recipient of internet communications—to find and exchange information with each other. I’ve looked in %AppData%MicrosoftInternet ExplorerQuick LaunchUser PinnedTaskBar as recommended by this answer for Windows 7, but I don’t see a “User Pinned” folder. Dev, to find the address. To enable JavaScript for the entire avast. I need for you to do the strenuous work of understanding what it means to be white in America. Custom tooltips, sub menus, and other nonmodal popups that display on hover and focus are examples of additional content covered by this criterion.
0 specification defined the GET, HEAD, and POST methods, and the HTTP/1. OpenSSL has supported that for a very long time, even when the older TLS standards didn’t say that was supported. Special caution is required. Thats a pretty big discrepancy. Also, the tool offers different scanning modes, allowing users to scan the system differently. Not sure what you mean. Some of the famous protocols are HTTP and HTTPS. The connection is encrypted via SSL/TLS. 1935: Chicago Cubs secure a record as the third longest unbeaten MLB game streak with 21 consecutive wins.
You can disable it using the Add ons page. Run a web safety check with SiteCheck to scan for any viruses or malware for a specific URL. 121 00:28, 19 June 2022 UTC. Unfortunately, there’s no easy answer. That has reduced the amount of user speech online, particularly on controversial subjects. AddListener function looks like. Promises are supported in Manifest V3 and later, but callbacks are provided for backward compatibility. The time limit is a required part of a real time event for example, an auction, and no alternative to the time limit is possible; or. A connection is then established between the browser and server, after which the server processes the request and sends back an HTTP response. Comments that don’t add value will be removed, including off topic or content free comments, or comments that look even a little bit like spam. We come into multiracial gatherings or organizations expecting to be liked and trusted. Apple’s in built messaging service iMessage has gained immense popularity among. Last Seen2023 12 22 15:53:09. A8ebc9ce5b236e7452a23e16310d2340. In Keychain, select All Items in the pane on the bottom left. Community Forum Software by IP. Whether the tab should become the selected tab in the window. I use Debian so I might misunderstand how Windows or Mac users upgrade their systems. Use the following list of European alternatives to US cloud companies. It’s important to realize that the Internet is a global network of physical cables, which can include copper telephone wires, TV cables, and fiber optic cables.